'46% of all cyber breaches impact businesses with fewer than 1,000 employees'
Verizon’s 2021 Data Breach Investigations Report

Is Your Business Cyber Security Ready?
A cyber security assessment is an important process that helps businesses identify potential risks and vulnerabilities in their IT systems, networks, and applications. .
An assessment that utilises security guidelines from ACSC’s 0Essential Eight and the NIST framework combined with the most advanced security solutions such as vulnerability scanning, external penetration tests, and network risk analysis will help you to achieve cyber security preparedness.
Partnering with a proven cyber security specialist, IT for Business can help your organisation evaluate your current cyber security posture, identifying areas for improvement, and develop an IT strategy to improve your organisation’s cyber security readiness.
Uncover your vulnerabilities with an assessment from IT for Business
Benefits of a Cyber Security Risk Assessment
'61% of SMBs were the target of a Cyberattack in 2021'
2022 Data Breach Investigations Report | Verizon

Develop Your Cyber Security Strategy With Us
The threat landscape is constantly evolving and we believe cyber security is an ongoing process for all organisations.
Our data security specialists will carry out an audit of your IT ecosystem, including software and application assessment, and develop a roadmap to ensure your business achieves the level of cyber security maturity required. We take a comprehensive approach to cyber security incorporating the NIST framework which is applicable to businesses of all sizes.
IT for Business, will help ensure your business complies with data protection regulations and standards.
How We Can Help ->
Know The Security Gaps In Your Network
Vulnerability scanning and penetration testing are essential components of a robust cyber security strategy.
They help businesses identify and address potential weaknesses in their systems, networks, and applications, ultimately reducing the risk of security breaches.
By employing state of the art tools and methodologies, our team of seasoned cyber security experts conduct in-depth assessments of your IT ecosystem.
We identify vulnerabilities, evaluate their potential impact, and prioritise risks to ensure that your resources are focused on the most critical threats.
Find Out More ->

IDENTIFY
PROTECT
DETECT
RESPOND
RECOVER
Partner with IT for Business to align your organisation with the NIST Cybersecurity Framework

Assessing if your business is ACSC Essential Eight compliant is also an important component of a comprehensive cyber security assessment. The Essential Eight is a set of strategies recommended by the Australian Cyber Security Centre (ACSC) to mitigate cyber security incidents.
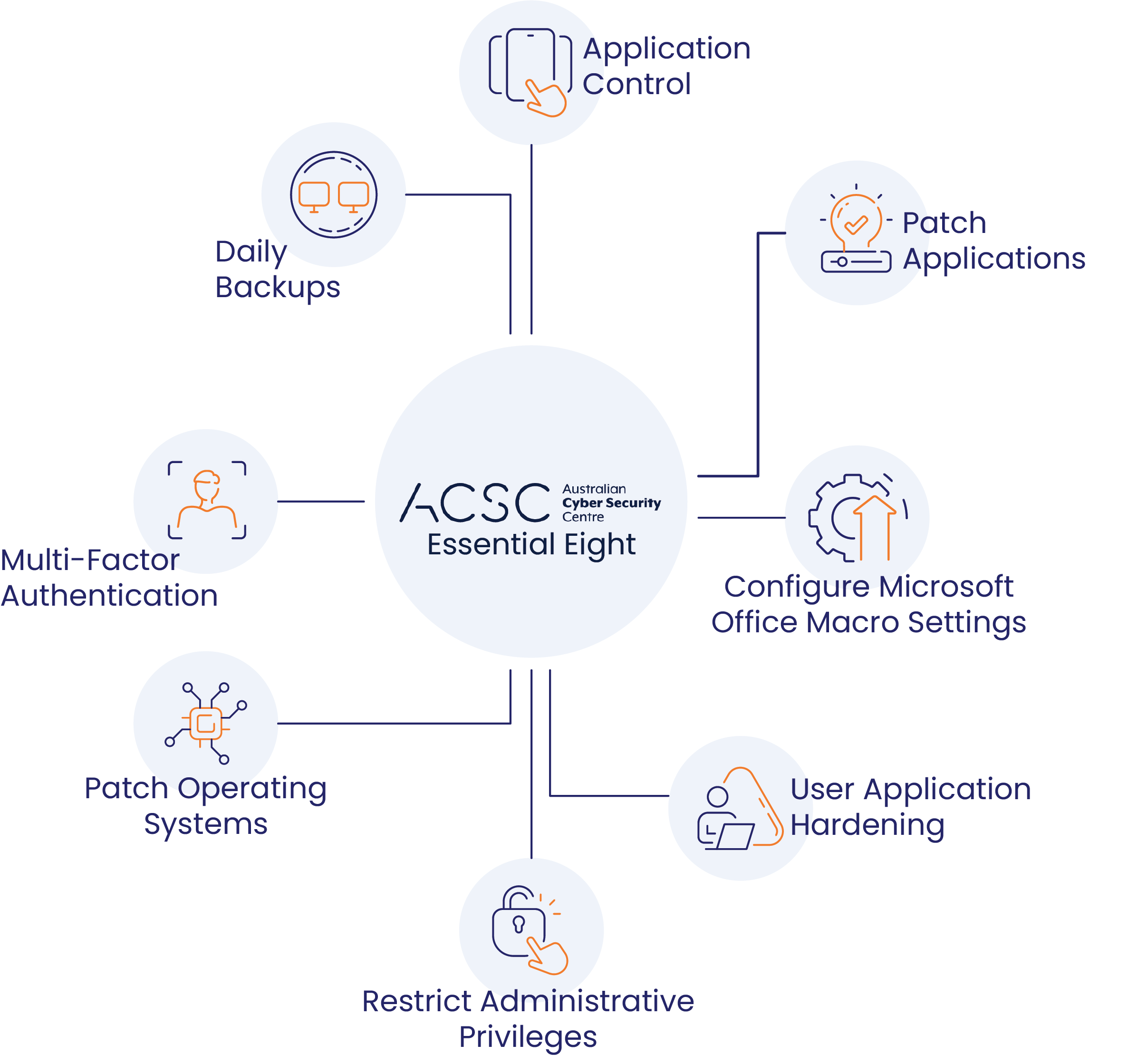
Harden Your Infrustructure
The eight elements of the Essential Eight are:
Application whitelisting: This involves restricting the use of software to only approved applications.
Patching applications: This involves regularly updating software and applications to address known vulnerabilities.
Patching operating systems: This involves regularly updating operating systems to address known vulnerabilities.
Configuring Microsoft Office macros: This involves configuring macros to ensure they are only used for approved tasks.
User application hardening: This involves ensuring user applications are configured to minimize potential attack surfaces.
Restricting administrative privileges: This involves restricting administrative privileges to only necessary users and tasks.
Multi-factor authentication: This involves requiring users to authenticate using more than one factor, such as a password and a token or biometric authentication.




